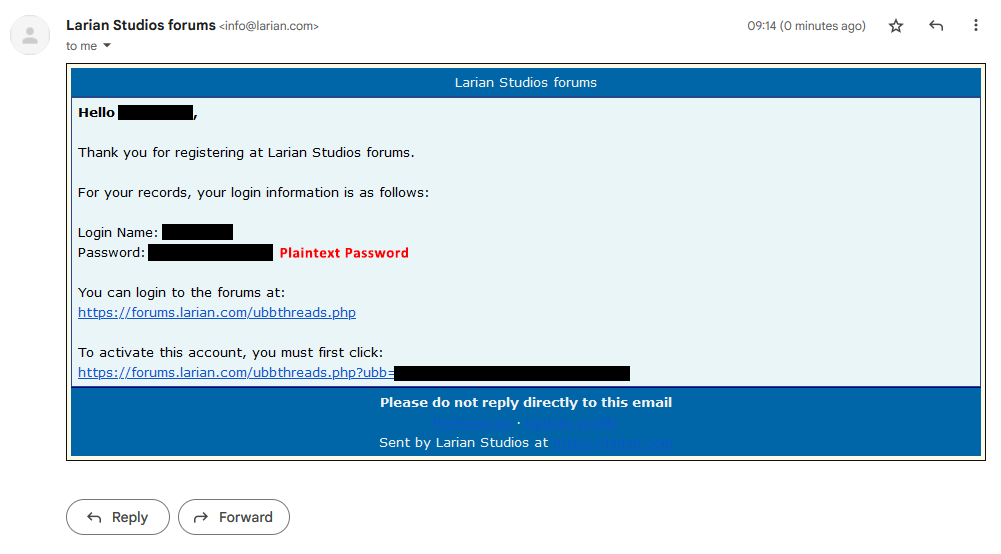
This thread is frustrating. Everyone seems more interested in nitpicking the specifics of what OP is saying and are ignoring that a forum sends you your password (not an automatically generated one) in an email on registration.
Larian stated on their forum they fixed this behavior and shifted to https 3 years ago. When this was linked several times in thread, people asked OP when this screenshot occured, and OP ignored the questions. Pretty clear that this is a very old screenshot of what is now a non issue.
What’s to discuss besides OP trying to stir up drama about issues that were resolved years ago?
this is a very old screenshot
What do you mean? It says “0 minutes ago”! Clearly it’s very recent! /s
Yeah this is the internet, not lame stream media that lies to you. /r
FWIW, it’s not fixed. The screen shot may very well be recent.
(The post in question was still bad reporting, though, for the reasons I detailed in my other comment here.)
Are you saying that the parent poster is giving incorrect information?
Edit: Oy, straight from their membership administration docs (emphasis mine):
Additionally, using the buttons below, you can delete the user, email the user’s password to him/her, (etc)
Are you saying that the parent poster is giving incorrect information?
Yes. mosiacmango’s comment repeated what others had already said (right down to specific words that I used in the original thread and here), and then jumped to this conclusion:
Pretty clear that this is a very old screenshot of what is now a non issue.
Everything about that statement is false. While the circumstances made it seem likely that the screenshot was old, it was not clearly so, and in fact, it turns out the issue is still present. I checked it. A registration email from the test I ran yesterday looked just like the screenshot in question, cleartext password and all.
Given that Larian reported the issue fixed three years ago, it’s possible that they fixed it locally and some time later upgraded to a new version of the forum software, thereby overwriting the local fix. Perhaps mosiacmango should have considered that before posting incorrect speculation as if it were fact.
Ouch… This should never be possible, in any world. If the password can be emailed, it can be seen. If it can be seen, it can be stolen.
It’s still an interesting case to discuss and learn about. We don’t ignore and forget about ww2, just because it’s over, do we?!
It’s disingenuous to pass off ww2 as a current event though.
Just wow, yeah. Nothing should ever send you a password in cleartext - once that’s been done, a MITM attack’s success rate just went to 100%.
It’s painless to use password resets if the person forgot the password. Never, ever should a password be in cleartext.
hunter2
Why did you put a bunch of asterisks at the bottom of your post?
I’m delighted you get the reference!
I’d be more worried if someone who uses the internet to such a degree that they use Lemmy over Reddit, on a programming forum, didn’t get the reference. This is famous hacker lore at this point.
Can you be worried for me, and fill me in?
This will explain it for you.
Oh, I’ve seen people do that crap on RuneScape back in the day. Not sure I’ve ever seen the meme though.
An issue if you’re reusing passwords. If not, every forgot my password email is also vulnerable.
A combination of bad practices could be… bad.
Edit: apparently around the same time, their forum was also lacking https. This would be an even easier vector.
It’s painless to use password resets
Ya and have they send you the (one-time) password in cleartext
(one-time)
You make it sound like an irrelevant detail, but that’s kind of the key part. If implemented properly, it’s only valid once and for a short period of time, which greatly reduces risk.
Sure. I just want to point out that there is valid case when passwords are sent in clear text.
In my experience it’s always a tokenized link, no clear text required.
Well, the tokenized link is essentially a clear text one time password. Not really any better than just a one time password except for the convenience that the user does not need to type it in. If someone gets hold of the link or password before you they can get access to your account.
I don’t see how’s either way better or worse as long as they force you to change the password upon login
And what is the token in the link?
Many years ago, I had forgotten my password to the Sprint websiteb so I could log in and pay my cellular bill. I had to call customer support to resolve this. After verifying my activity, the support agent read me my existing password one letter at a time. While this was alarming, I was amused she had to spell out a somewhat obscene phrase for me. This was maybe 20 years ago and I no longer use Sprint.
I no longer use Sprint
I mean, nobody else does either.
MITM attack’s success rate just went to 100%
No, it didn’t. It’s stupid and shouldn’t be done, but all ham nowadays is encrypted.
I know that because I’ve been running my email server for some years now, technically breaking one of the RFCs for not allowing unencrypted connections. Zero email has been missed.
While I agree that likely most SMTP traffic is sent encrypted these days, you simply cannot be sure. Just because you received something over an encrypted connection doesn’t mean that relays in between also used this. The webserver could have handed over the email unencrypted to an SMTP server for all you know. And even if an encrypted connection was used the mail might still have been copied to a log on the SMTP server. Email is unfortunately inherently unsafe.
Fair point. Although it’s very rare to have actual 3rd party relays in path.
I think the OP of that post would have had a better reception if they had:
- Responsibly disclosed what they found, rather than using it to stir up drama on social media.
- Mentioned that it’s just a web forum account, not connected to game accounts or anything else of value.
- Targeted the software vendor (https://www.ubbcentral.com/) instead of picking on one particular customer who used that software.
- Refrained from spreading misconceptions and unfounded assumptions about how the technology works.
- Responded to the reasonable follow-up questions, such as those that came when readers discovered that the problem was reported fixed three years ago.
People in that thread responded with skepticism and criticism to an irresponsible, misdirected, misleading, alarmist mess of a post. That’s hardly surprising.
This was hashed out pretty thoroughly in that thread.
The initial concern over the password being stored in plaintext was shown to be a mistaken assumption, and it was made clear that this kind of email doesn’t happen anymore, it’s an outdated problem.
No need to keep the discussion going past that, is there? Much less spread it around?
Sending passwords via email Will compromise any passwords sent via email. Regardless if the password is stored anywhere in the process if the password is sent via email it is compromised and no longer safe to use. Email is not end and encrypted you have no idea who’s running the mail exchange servers that your email follows, it’s entirely possible for this company to store that password in a log dealing with their email servers. Password sent via email should be considered immediately compromised and any sites following a practice like this should not be trusted with standard passwords which you shouldn’t be using anyway.
Right, and everyone agreed that wasn’t the greatest practice. Two years ago.
This thread from two days ago was bringing attention to an issue that was fixed two years ago, and calling it out as if it was a different problem than it was.
It’s good to have discussions about security best practices, but this thread is pointless. This problem is simply not there anymore.
Email isn’t end to end encrypted but, but it generally is encrypted. The people who will have it are the sender (who already have the password since they created it) and whoever runs the recipient’s mail server. Which is hopefully someone the recipient trusts.
From the sounds of it, this was a password that the server randomly generated, so it’s never been used before, and you are forced to reset the password as soon as you use it, so it’ll never be used again and they do treat it as “immediately compromised”.
Hardly state of the art security, but it also doesn’t really have any major problems… especially since this is for a forum.
Email often is end to end encrypted these days. It’s just that there are no guarantees.
Sending passwords via email Will compromise any passwords sent via email.
100%. But that is a different problem and a different attack vector than storing passwords in plain text for authentication. When reporting security issues, it’s important to be precise.
hashed out
heheh
People weren’t really nitpicking.
- it’s obviously bad to send an email with a plaintext password
- the website owners had apparently already resolved the issue
- it does not mean the passwords were stored in plaintext
- the OP sounds like a skiddie in a bunch of comments and doesn’t seem to understand how most websites with auth work
it does not mean the passwords were stored in plaintext
This is debatable. Yes, there is a chance the email is being generated and sent on the fly, before the password is stored. But in situations like this there is a much larger chance it’s being stored in plain text.
They have said it is being hashed for storage: https://forums.larian.com/ubbthreads.php?ubb=showflat&Number=669268#Post669268
I can’t fault the OP though, if I received such an email I would assume it is stored in plain text and be similarly upset.
Reversible hashed password storage isn’t meaningfully better than clear text.
- The key to reverse the hash is typically (necessarily) stored in the same infrastructure as the password. Bad actors with access to one have access to the combination.
- Even if an attacker fails to exfiltrate the key to the reversible hash, it’s typically only a matter of days at the most before they can reverse engineer it, and produce plain text copies of every password they obtained the hash of.
A reversible hash provides a paper thin layer of protection against accidental disclosure. A one way hash is widely considered the bare minimum for password storage.
Anyone claiming a password has been protected, and then being able to produce the original password, is justly subject to ridicule in security communities.
The one they were sending at registration was prior to hashing. It would not be reversible afterwards.
That’s technically less terrible, then.
Good for them. /s
Edited to add the /s for clarity, because the NIST recommended remediation in 2023 for emailing a password is “burn everything down and pretend the organization never existed”. /s
Again, adding that /s since that’s not actually what NIST says to do, and I am, at best, paraphrasing.
I wasn’t trying to claim what was happening here, simply that one (extremely) bad practice increases the chance of another.
But in situations like this there is a much larger chance it’s being stored in plain text.
I suppose, but OP said in the title that the passwords were being stored in plaintext, despite that not being the case.
Using “we use a reversible hash” to claim “we don’t store passwords in plain text” is the “corn syrup is not sugar” of the cybersecurity world.
It’s technically correct, while also a bald faced lie.
Not sure what you mean here, this is what the forum post said:
After emailing (admittedly not current best practice), the passwords are hashed and only the hash is stored.
Also if they store a copy of that email they’re effectively storing the password in plaintext even if they e properly made a salty hash brown for the database.
Yep. And their own email system is probably also logging it somewhere. So are various servers along the way to it’s destination.
Why wouldn’t it be generated and sent immediately? If someone has the inclination to do this type of thing, they probably also want to do things synchronously and immediately.
Because one egregious decision normally begets another.
Look at it this way, if you walk into a pizza joint and there are roaches wandering around on the walls, is it not more likely the food is also unsafe to eat?
Yes, this could just be one horrible decision, but this decision shows you where the mind of the developer/team was when thinking through their security.
You actually agree with me more than you disagree. If they have the mentality to send out clear text passwords, they probably don’t hage the natural talent to design an asynchronous system.
Everyone seems more interested in nitpicking the specifics of what OP is saying and are ignoring [the actual point]
This is the experience working in a professional software development setting, yes.
Everyone seems more interested in nitpicking
Actually, not everyone in that thread is nitpicking. There’s one comment that’s just a helpful hint.
But yes, nitpicking is fun. I’ll see myself out.
No, I’ll allow it, this is a good post. Not even being sarcastic, did me a grin haha
Uh, I seem to recall this happening when I made a Larian account. What happens is you give them your email, they make your account, and email you a temporary password. The temp password is shown in plaintext, as the email shows. Once I saw the email, I logged in to finalize my account and change my password to something secure. It’s not the most modern process, but I wasn’t really that concerned either.
OP misspoke, lied, or it was different when you joined then.
This was just recently since BG3 came out. Since I first saw this drama I was pretty sure OP was misrepresenting the situation.
OP of that thread was talking about how (they think) the password was stored in plain text instead of this “tree” you’re talking about. The discussion on that was not a nitpick.
deleted by creator
The forest is bad practice with passwords, since you get an email of your password after setting it.
The tree is OP not knowing how to describe why it’s bad and saying the wrong reason why.
I mean, there were a lot of forests in that thread. Like how it was an old screenshot and they don’t do those emails anymore. Or you shouldn’t re-use passwords anyways. I don’t blame people for missing 1 or 2 forests.
The number of people accepting email for some magic thing without in-between mechanisms is ridiculous. If it’s sent in an email you should 100% consider it to be stored in plaintext in multiple places. There is incredible amount of machinery between your
mail()call and the end user reading that email, on both the sending and receiving end. For example, my spam filter (rspamd) will likely store a copy of it for a while, and that’s not unique to it.What’s in the database is not really relevant. Only the worst instance of storage counts.
Everyone seems more interested in nitpicking the specifics of what OP is saying
Yep. That’s how security works. You have to nitpick the specifics.
The reality is nobody has invented a perfectly secure authentication system that is easy to use (for example, allows easy recovery when people forget their password which for any large service will be tens of millions of times per day).
Attempts have been made - passkeys being the latest one - but they’re not even remotely easy to use as soon as you step slightly out of the most common path (such as using the web browser that is provided by the company you’re logged in with… try to use Chrome with an Apple passkey, or Safari with a Google passkey, and you’re going to stumble into usability issues).
Passwords are not considered secure wether they’re sent in a plaintext email or not. They can be secure, if used properly, but 99% of users don’t follow best practices. As a result almost every web service in the world is insecure and it’s the nitpicky details that matter.
Sending a secret to an email address is a standard step during registration for almost any service.
But the thing is that you should never have access to the plaintext password and thus you should never be able to receive it in an email. You should store the salted hash of the password instead of the password itself.
These kind of forums don’t store the plaintext password, they send an email while in memory, and hash them afterwards. Still bad security, but it’s not storing it in plaintext.
It’s storing it in plain text in at least one third party’s database. Indeed, it’s not stored in plain text locally, it’s doing something much worse
But you are supposed to change that generated password as soon as you use it to login. Now I have no idea about these forums, but you’d expect the software to enforce that need to change
It’s still stupid because people reuse password. They shouldn’t, but they do. If it’s one time login, make it a token. There’s zero reason to ever email a password, period
But your password should never reach the server. It should be hashed already at the client and then salted at the server with a random hash. Then you store the salted hash
When I say “nitpicking the specifics” I mean OP is saying things like the password should never be unencrypted in memory in the same comment as mentioning things like the password in plaintext in the email and folks are more interested in browbeating over the first thing rather than acknowledging the second as a problem. I see this behavior far too often in tech spaces online. People are often more concerned with being pedantic and technically correct than anything else.
The person you’re responding to is doing the exact same thing you are complaining about, and finished their comment with something obviously wrong. They are not arguing in good faith
The only issue I can see is why are you sending the password to the person in the email at all just seems redundant… I think I may have run into a tree though.
deleted by creator
Then you realize that some of the game-related 2fa apps out there are more secure than a lot of online banking credentials.
If you’re following proper security procedures you wouldn’t be using the same password for anything else, so they are overly concerned about the wrong things while parading being top notch security wise while not doing it themselves.
Yeah it’s an issue, but only an issue if you’ve set yourself up to be vulnerable.
I agree. Unfortunately many folks who are attracted to security issues and topics don’t have a great holistic view of things. The idea of security is that something can go wrong and you are still ok, and that you apply context appropriate measures. Of course sending a password through email isn’t good, but it’s a gaming forum. A security conscious individual should have randomly generated passwords for everything and no reuse. Likewise, it wasn’t a bank or a security company, it was an old forum software for public discussions, so contextually this isn’t a top concern.
The cherry on top is that it appears to have been an old screenshot and already addressed.
Its weird how there seems to be a group dedicated to creating and subsequently reporting on imagined faults within Larian. There have been a few articles and now that guy who used an out of date screenshot to make an unfounded claim.
They aren’t perfect, and there are a fair number of things issues in BG3.
Like that it has a number of the same issues as their previous game, Divinity Original Sin 2. Suggesting that they didn’t see those issues as issues, or didn’t see a need to change their process to correct them.
imagined faults
Sending passwords in plaintext in emails is not an imaginary problem.
Nope, but using that to claim that they’re storing the passwords in plain text is.
Everyone seems more interested in nitpicking the specifics of what OP is saying and are ignoring that a forum sends you your password (not an automatically generated one) in an email on registration.
I see it as a non issue because Larian has a previous post up, in a timeframe window of acceptable lack of visible action, about them finding a solution to that problem.
If nothing has been announced in a month or so, then it starts becoming a problem again.
It’s criticism directed at a service provider, not users. Service providers should assume users reuse passwords. Security is about protecting everyone.
Than direct it at the service provider? Oh wait it got fixed a while ago.
Also where does their liability stop? Should they also just assume everyone is compromised? Where does the users onus come into play? I guess they shouldn’t send password resets than, since they should assume that their email is compromised already….
Yeah that’s actually a terrible idea if they must assume that they must protect everyone. Sorry can’t reset your password your email must be compromised.
This is slippery slope bullshit and you know it. I’m not saying providers should have to magically prevent anything. I’m only saying they shouldn’t send you your password in an email. Crazy take, I know.
Also, with regards to it already being fixed or not, when I made this thread I hadn’t seen anything about that in the other thread. I’m more just annoyed that people want to dunk on people with supposed gotchas while acting like sending a password in an email is okay somehow.
No it’s not slippery slope in this case, it’s what you’re suggesting and why it’s utter bullshit. But yes of course that’s the obvious defense to take there.
You’re not only saying that, you said that they need account for everything. Two totally different things. Can’t have X and not have Y.
Sending a password is okay in quite a few scenarios, you’re talking to broad again her. Also, maybe make sure you know the story before jumping on as well…? You’re making the issues worse not better.
Definitely. You don’t send passwords, ever, even if it’s encrypted by a quantic email server from the future.